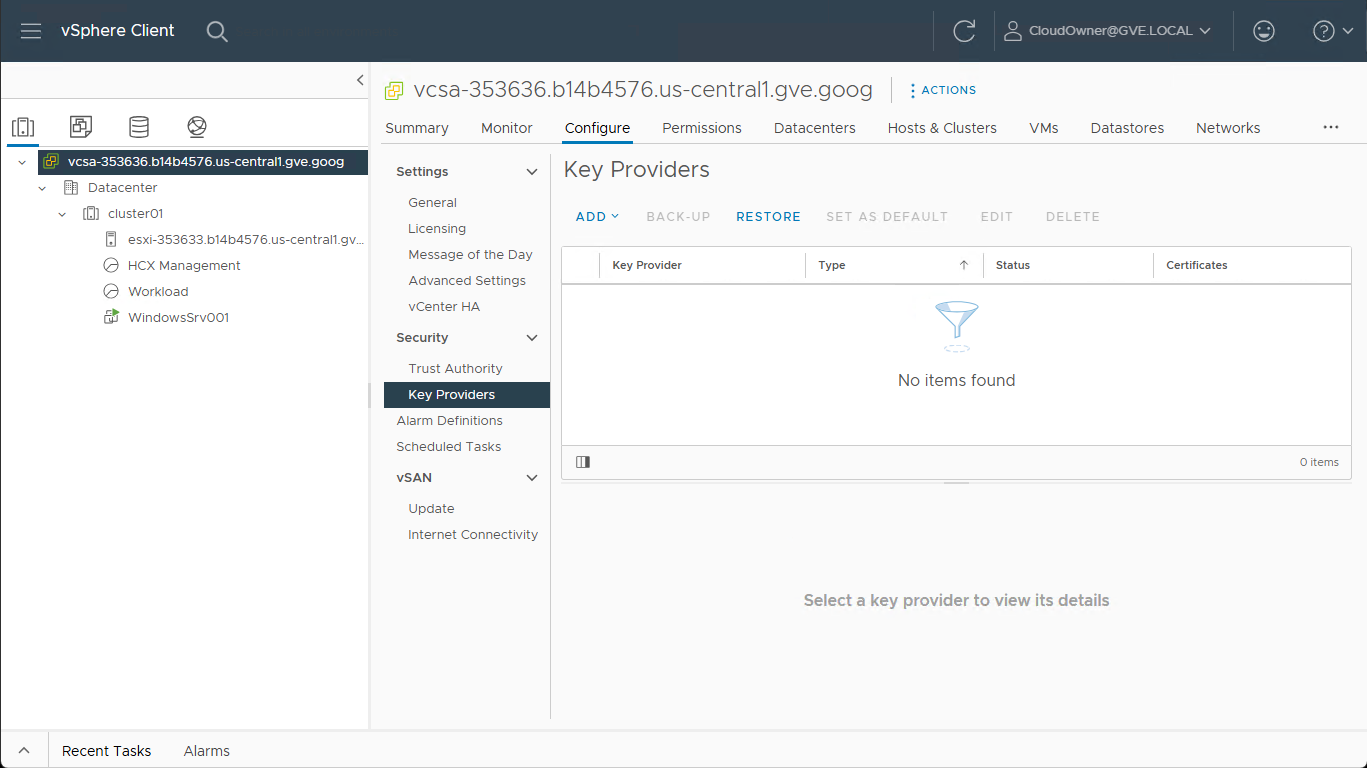
Recently, I needed to access the Key Providers screen within my private cloud’s vCenter instance to configure the default provider for vTPM. I quickly remembered that the CloudOwner account within Google Cloud VMware Engine (GCVE) doesn’t have enough permissions to access or edit the KMS settings.
Since the prior method of elevating privileges with the CloudOwner account has been deprecated, you must now use one of the solution-user accounts (which can be modified through the cloud shell). The gcloud command syntax for these tasks can be found within the Google Cloud documentation page titled Elevate VMware Engine Privileges.
Step 1: Reset the solution user account credentials
If this is the first time using a particular solution user account, the first step is to reset the credentials.
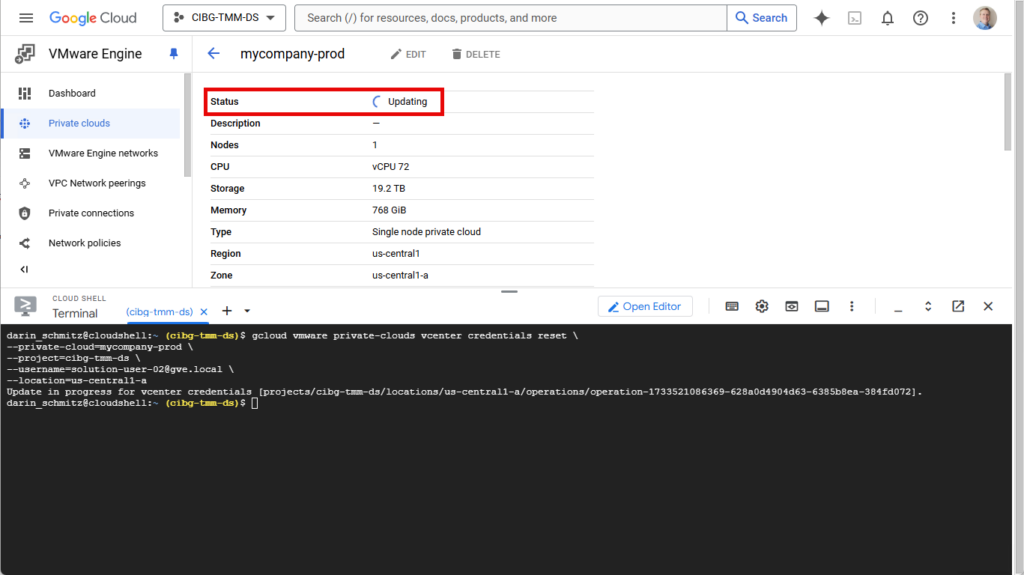
For my private cloud shown in the screenshot, I used the following command:
$ gcloud vmware private-clouds vcenter credentials reset \
--private-cloud=mycompany-prod \
--project=cibg-tmm-ds \
--username=solution-user-02@gve.local \
--location=us-central1-aOnce the command is issued, it can take several minutes for it to run the workflow that resets the credentials. During that time, the private cloud status will show Updating as the task is in progress.
Note: Just as a heads up, while the workflow is running, I was not permitted to access the KEY DETAILS for the management appliances (for example, to copy the vCenter password), so you just have to wait until it finishes.
Step 2: Get the solution user password
Once the process was finished and the private cloud status returned to Active, you can then issue the command to retrieve the password.
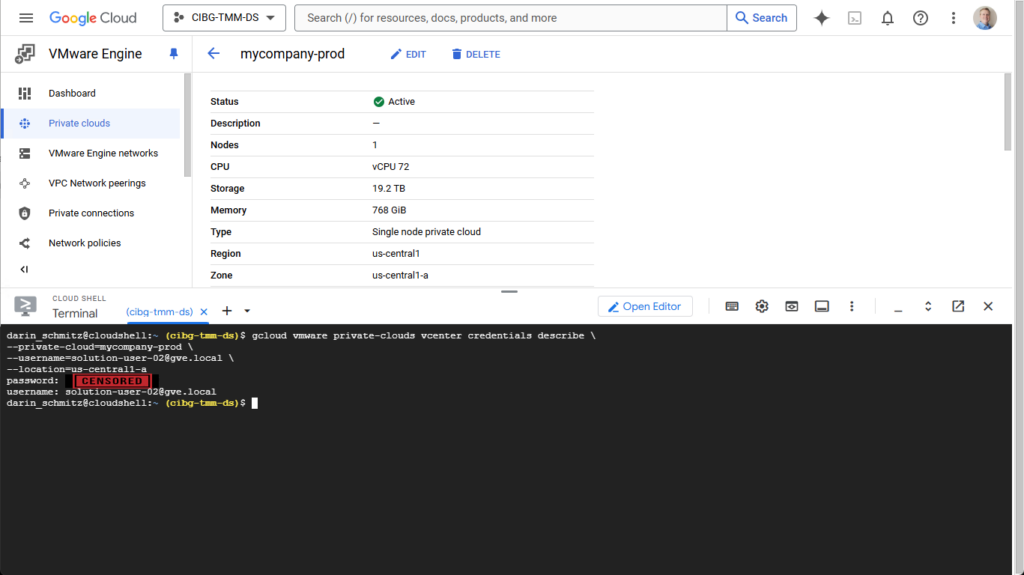
Following along with my example, here is the command that I issued to get the password.
$ gcloud vmware private-clouds vcenter credentials describe \
--private-cloud=mycompany-prod \
--username=solution-user-02@gve.local \
--location=us-central1-a
password: a1B2c3D4e5F6g7*P
username: solution-user-02@gve.localOnce I had the password for the solution-user-02@gve.local account, I was finally able to log into vCenter, and configure the Key Providers settings.
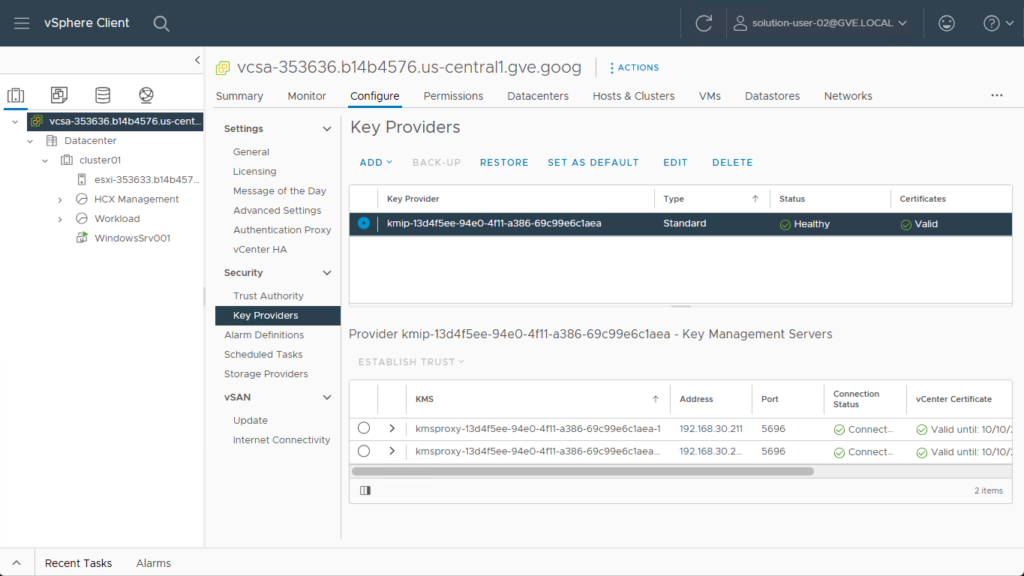
Conclusion
With the ‘gcloud’ command-line tool, we successfully modified a solution user account to gain elevated privileges within our GCVE private cloud’s vCenter instance. By resetting credentials and retrieving the password, we gained access to critical features like configuring key providers for vTPM, but this also allows you to configure third-party applications. Remember that even though you have elevated privileges, there are still Forbidden actions that are not permitted.